Android Exploitation makes Android Lifeless
Android Exploitation Vulnerability : Leaves Android Screen Dead !
An Android vulnerability has been discovered that leaves the Phone Dead .Well this is a Treat for Android Exploitation Enthusiasts .The Vulnerability that has been discovered in Android can render a phone apparently dead – silent, unable to make calls, with a lifeless screen. And this vulnerability is present from Android 4.3 (Jelly Bean) up to the current version, Android 5.1.1 (Lollipop). In this artical hacking loops brings you this vulnerability explaining the flaw and the origin , though we also plan to share the Proof of concept in latter posts.
Android has been very ubiquitous since the beginning and popular for its vulnerabilities . This vulnerability is present in the versions Android 4.3 (Jelly Bean) up to the current version, Android 5.1.1 (Lollipop) which account for likely than half of Android devices in use today.
No patch has been issued in the Android Open Source Project (AOSP) code by the Android Engineering Team to fix this vulnerability though the vulnerability has been reported by Trend Micro in late May.
This vulnerability that leaves the Android Phone Screen to be lifeless can be exploited in two ways:
- either via a malicious app installed on the device
- through a specially-crafted web site.
If the Attacker uses the first technique , using the malicious Application on the Device then it can cause long-term effects to the device: an app with an embedded MKV file that registers itself to auto-start whenever the device boots would case the OS to crash every time it is turned on.
In some ways, this vulnerability is similar to the recently discovered Stagefright vulnerability.
Both vulnerabilities are triggered when Android handles media files, although the way these files reach the user differs.
Both vulnerabilities are triggered when Android handles media files, although the way these files reach the user differs.
Android Vulnerability Description
The vulnerability lies in the mediaserver service, which is used by Android to index media files that are located on the Android device. The Media Server service cannot process correctly if a malformed video file using the Matroska(.mkv format video file) container (usually with the .mkv extension). When the Media Sever Service / Process opens a malformed MKV file, the service may crash !! And with it, so will the rest of the Android operating system.
This vulnerability is caused by an integer overflow when the mediaserver service parses an MKV file. It reads memory out of buffer or writes data to NULL address when parsing audio data. The source code below – found in the frameworks/av/media/libstagefright/matroska/MatroskaExtractor.cpp file – shows the vulnerability in detail:
865 size_t offset = 1;
866 size_t len1 = 0;
867 while (offset < codecPrivateSize && codecPrivate[offset] == 0xff) {//codecPrivate is controlled by the mkv file
868 len1 += 0xff;
869 ++offset;
870 }
871 if (offset >= codecPrivateSize) {
872 return ERROR_MALFORMED;
873 }
874 len1 += codecPrivate[offset++];
875
876 size_t len2 = 0;
877 while (offset < codecPrivateSize && codecPrivate[offset] == 0xff) {
878 len2 += 0xff;
879 ++offset;
880 }
881 if (offset >= codecPrivateSize) {
882 return ERROR_MALFORMED;
883 }
884 len2 += codecPrivate[offset++];
885
886 if (codecPrivateSize < offset + len1 + len2) {//len1 or len2 maybe 0xffffffff, then integer overflow happened
887 return ERROR_MALFORMED;
888 }
889
890 if (codecPrivate[offset] != 0x01) {
891 return ERROR_MALFORMED;
892 }
893 meta->setData(kKeyVorbisInfo, 0, &codecPrivate[offset], len1);//crash in here
What Happens To my Android when Exploited
The mediaserver service continuously restarting after the exploit is triggered .This Android Vulnerability when exploited by an attacker will cause the device to become totally silent and non-responsive. This will leave the Android Phone Lifeless or Dead .
The following happens when the Vulnerability is EXPLOITED :
- No ring tone, text tone, or notification sounds can be heard. The user will have have no idea of an incoming call/message, and cannot even accept a call. Neither party will hear each other.
- The UI may become very slow to respond, or completely non-responsive. If the phone is locked, it cannot be unlocked.
Keep Reading our posts for further Updates on Android Vulnerabilities and Exploitation Techniques .
Android Forensics Tutorial 4 – Unlock Android Pattern Lock: In our previous Android Forensics Tutorials, we have learned about Directory structure, File Systems, Data Acquisition methods and how to copy sdcard data to your computer drive. In this Android Forensics Tutorial, we will learn about How to unlock or recover Android Pattern Lock or pass code. As we all know, currently android supports three basic types of pass codes to lock Android Smartphones namely Pattern Lock, PIN and Alphanumeric Code. Each of these pass codes can be hacked via using a different approaches. Each method has its own limitations. Today i will explain how to unlock Android Pattern Lock of a rooted device via USB debugging method.

Forensics Tutorial 4 – Unlocking Android Pattern Lock
If USB debugging is enabled, then bypassing the lock code can be done in a matter of seconds. Imagine an attacker who wants to get access to his friend’s files and applications on his Android mobile. You can first ask his handset for some false reason, to make a call, for example, and turn on the USB debugging under Settings à Developer Options à USB debugging; and then hand over the mobile back to him. So later, at some convenient time, when you get access to the device, you can exploit it using any of the following ways discussed in this article. Now adb (Android Debugging Bridge) is primarily a command line tool that communicates with the device. ADB is bundled with the Android platform tools. To explain in simple terms, this is what happens when you communicates with adb(Android Debugging Bridge):
- An adb daemon runs as a background process on each Android device.
- When you install Android SDK on your machine, a client is run. The client can be invoked from shell by giving an adb command.
- A server is also run in the background to communicate between the client and adb daemon running on the Android device.
Now lets learn how to Hack Pattern Lock of any Android device in less than 5 minutes. The only condition required is that, smartphone should be rooted.
Unlock Android Pattern Lock or Pass code :
- Connect the device to the machine where Android SDK (including platform tools etc.) is installed.
- Open command prompt and type cd C:\android-sdk-windows\platform-tools>adb.exe devices
- The device will be identified by the adb if everything is going fine.
- Connect to adb shell by typing : adb.exe shell
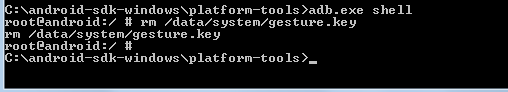
- The terminal appears giving you access to shell. Now type rm /data/system/gesture.key. This is the file where pattern is stored.
- Restart the phone and you will still observe that the device is asking for the pattern. You can draw any random pattern and unlock the device.Below is the screenshot of above process :
That’s all for today friends. We will learn other Forensic Methods in detail in future articles.
List of Previous Android Forensic Tutorials :
Hope you all have enjoyed our Forensics tutorial on Unlock Android Pattern Lock. Keep Learning !! Keep Connected!! Sharing is Caring!!

No comments